Protect Your Business from Zero-Day Threats with Threatlocker – The Ultimate Zero Trust Endpoint Security Solution
In 2020, the average ransom demand for SMBs was around US$233,817. Investing in ThreatLocker® can provide the proactive security and defenses your organization needs from falling victim to zero-day malware, ransomware, and other malicious software attacks.


Protect Your Business from Zero-Day Threats with Threatlocker – The Ultimate Zero Trust Endpoint Security Solution
In 2020, the average ransom demand for SMBs was around US$233,817. Investing in ThreatLocker® can provide the proactive security and defenses your organization needs from falling victim to zero-day malware, ransomware, and other malicious software attacks.

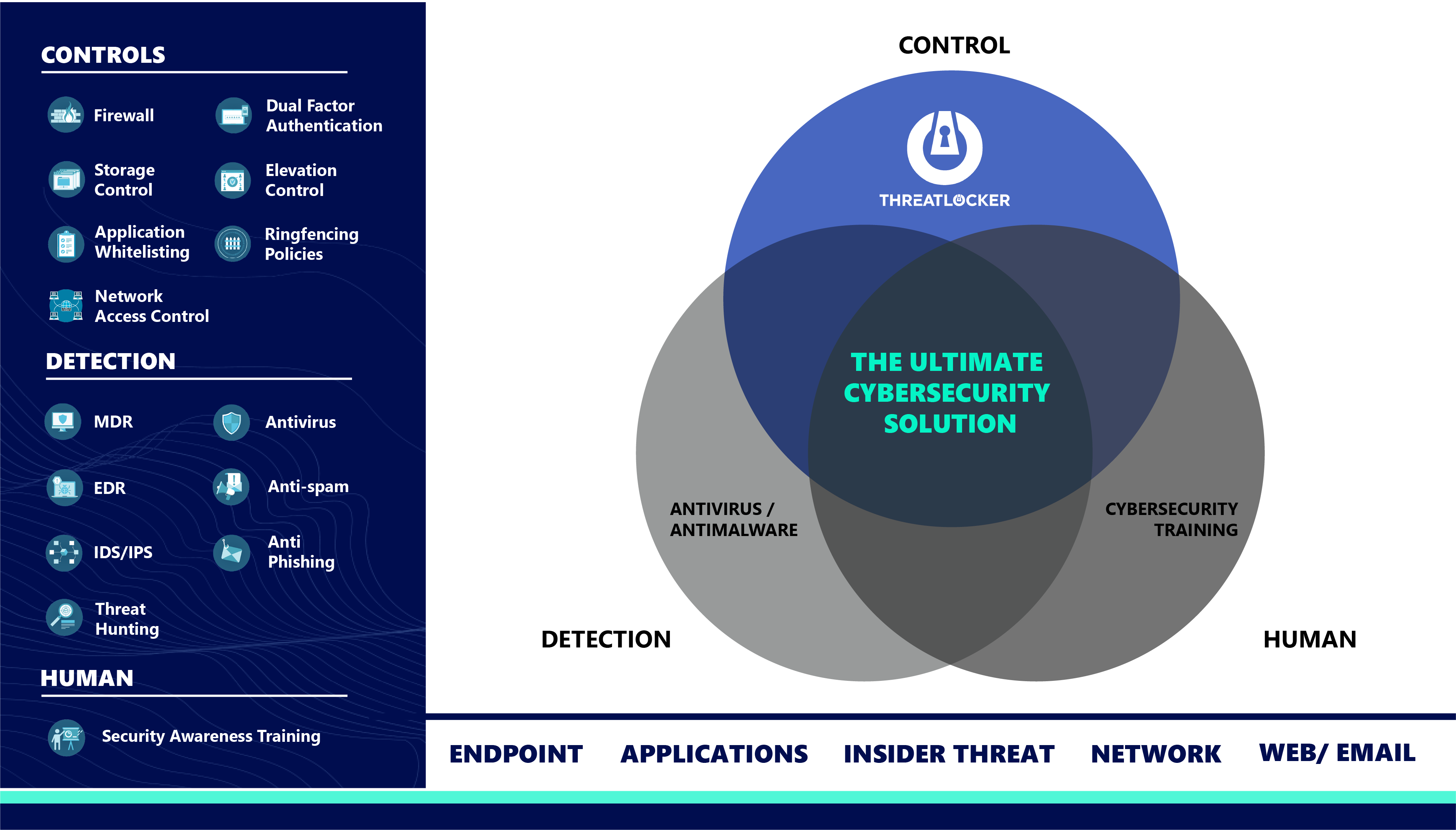
ThreatLocker completes your cybersecurity stack on top of your existing threat detection solutions and security awareness trainings
ThreatLocker completes your cybersecurity stack on top of your existing threat detection solutions and security awareness trainings.

Application Allowlisting
What is Application Allowlisting?
Application Allowlisting denies all unapproved software from running by default, preventing ransomware and other malware.
- Default deny any application from running on your device.
- Control applications easily from dashboard.
- Auto learning of applications used in your organization.
- Firewall-like Policies: Granular control over application access with options to permit, deny, or restrict.
- Time-Based Policies: Automatically permit access to applications for a specified time, and block them after the policy expires.
- Built-In Applications: ThreatLocker automatically adds new hashes for application and system updates, ensuring your applications are always up to date.

Application Ringfencing
What is Application Ringfencing?
Ringfencing prevents unauthorized access to your files and prevents applications from launching other programs that can be exploited against you, even those that are permitted in your allow list.
- Creates a fence for each application.
- Applications are not permitted to speak to each other unless granted.
- Provides template for easy execution.
- Protect Against Fileless Malware: Limit the actions that applications can perform to prevent fileless malware attacks.
- Enhance Security with Granular Application Policies: Control how applications interact with other applications, network resources, registry keys, files, and more.
- Prevent Application Attacks: Prevent application hopping and other types of attacks by limiting the access that applications have.
- Safeguard Your Files: Easily choose which applications have access to your files, enhancing your overall security posture.
Powerfully Simple, Seamlessly Compatible
Powerfully Simple, Seamlessly Compatible
Protect Your Business with Confidence
Over 25,000 companies have already chosen ThreatLocker to secure their networks and endpoints.
Deploy in a Snap
With ThreatLocker’s hassle-free deployment, you can have everything up and running in just one hour.
Perfect for Companies of Any Size
Whether you’re a small business or a large enterprise, ThreatLocker gives you the protection and control you need.
Take Total Control
With ThreatLocker, you have complete control over what software can run on your systems, ensuring maximum security and peace of mind.